With numerous examples in the news, it should come as no surprise that cybersecurity attacks are on the rise.
Verizon’s 2016 Data Breach Investigations Report summarizes 64,199 cybersecurity incidents including 2,260 breaches with confirmed data loss that occurred during 2015 alone1. Intel Security / McAfee’s conservative estimate of the annual cost to the global economy from cybercrime is more than $375 billion in losses2. These attacks targeted all types of public and private organizations and industries, highlighting the fact that there are no network connected systems that are immune from online threats.
Smallsat ground networks are no exception—they, too, are exposed to an increasing number of targeted cyberthreats, including those attempting to exploit vulnerabilities not found in most traditional Information Technology (IT) network environments.
This article is intended to be a security primer for smallsat ground network operators, discussing security best practices such as Information Assurance (IA) hardening and continuous monitoring; leveraging frameworks such as Defense Information Systems Agency (DISA) Security Technical Information Guides (STIGs); and tools such as Security Information and Event Managers (SIEMs) and Security Content Automation Protocol (SCAP) compliant applications.
Mission-Unique Attack Surface
Ground networks have unique cybersecurity challenges such as: mission-unique equipment and applications, specialized protocols; high regression test costs and tight budgetary constraints. Mission-unique equipment found in satellite ground networks primarily consists of radio frequency (RF) signal processing gear and test equipment such as oscilloscopes, spectrum analyzers and channel simulators.
Specialized protocols and applications include Software Defined Radio (SDR) and Command and Control (C2) suites among others. These niche devices, applications and protocols present unique attack surfaces for potential exploitation. As end-to-end IP architectures become mainstream in smallsat ground networks, additional security challenges are introduced.
Unlike traditional network environments, which are primarily concerned with IP based attacks, satellite ground networks also need to consider RF based threats. For example, in addition to Internet based scans, amateur satellite enthusiasts are on the constant lookout for new satellite feeds detectable using low-cost commodity RF hardware and open-source software.
Smallsat Tip: Attacks like this demonstrate that, when possible, it is important to encrypt not only command and control links, but also telemetry / downlink channels. Even simplex telemetry containing unencrypted metadata can lead to potential exploits.
One such exploit is described in a report by Kaspersky Labs which claims that a Russian-speaking spy gang known as Turla uses hijacked satellite IP addresses of legitimate users, sent as unencrypted metadata, to steal data from other infected machines in a way that hides their malware command and control server3.
Resources and Best Practices
Recognizing that smallsat ground network operators may lack the resources and budgets of traditional satellite operators, it is beneficial to leverage lessons learned, along with frameworks, and tools from Government and Industry to help better defend their networks.
The NIST Special Publications (SP) library provides a wealth of information and resources that can be leveraged by smallsat ground network operators who are just getting started developing a security program. The SP800 series consists of Computer Security related guidelines, recommendations and reference materials. The new SP1800 series Cybersecurity Practice Guides provide practical user-friendly guidance to help public and private sector users adopt a standards-based cybersecurity approach.
Security Process
Before diving into the technical controls that are often the initial thought for network engineers, a solid security program must include policies and procedures to help manage the security needs of the organization. NIST SP guides and frameworks can be used to help establish and drive policy. Tools, such as the Risk Management Framework and Contingency Planning Guide, can help an organization get a strong starting point for security and IT infrastructure beyond purely hardware related controls.
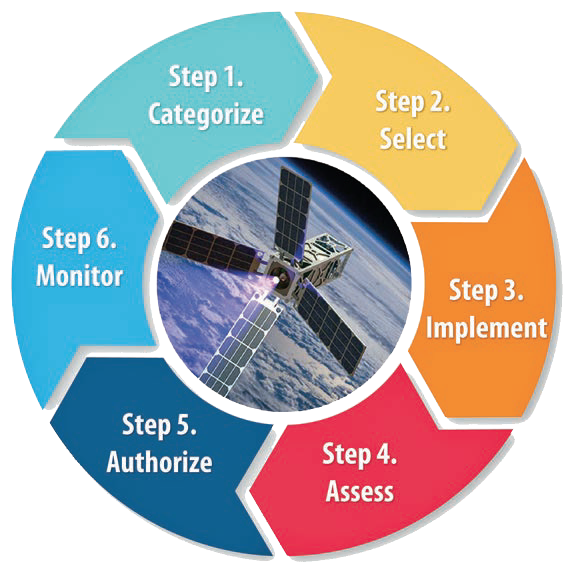
An overview of the Risk Management Process is contained in NIST SP 800-37 Guide for Applying the Risk Management Framework to Federal Information Systems. The Risk Management Framework is an iterative process consisting of the following six steps: Categorize, Select, Implement, Assess, Authorize, and Monitor, as illustrated in Figure 1.
Step 1: Categorize the information systems and the information they process, store and transmit, based on a risk/impact analysis.
Step 2: Select the baseline security controls and tailor as needed to meet the organization’s risk assessment.
Step 3: Implement the selected security controls and document how they are employed within the information system and its operational environment. DISA STIGs and SCAP tools can be used to help automate and document portions of this step.
Step 4: Assess the security controls to ensure they are implemented correctly. Assessment can be accomplished using automated vulnerability scanners (i.e.: Nessus) or through manual inspection and validation. DISA STIGs and SCAP tools can be used to help automate and document portions of this step.
Step 5: Authorize operation of the information system based on determination that residual risk is acceptable to the organization.
Step 6: Monitor information system security controls on an ongoing basis. Practice good configuration management to document changes to the system and operational environment. SIEM and SCAP tools can help automate and document portions of this step.
Smallsat Tip: Each step in the process can be tailored to meet the specific needs of the organization.
System Hardening
NIST 800-53 provides general guidance for security controls; however controls do not always translate easily into actionable items that can be implemented on a system. DISA Security Requirements Guides (SRGs) are a compilation of Control Correlation Identifiers (CCIs) which break down NIST SP 800-53 controls into actionable items, grouped into specific technology areas such as operating systems, applications, networking devices, and policy.
DISA STIGs are validated hardening guides, updated quarterly for major operating systems, applications and network hardware. Configuring systems in accordance with applicable STIGs can help to remove or mitigate configuration vulnerabilities present in satellite ground network devices.
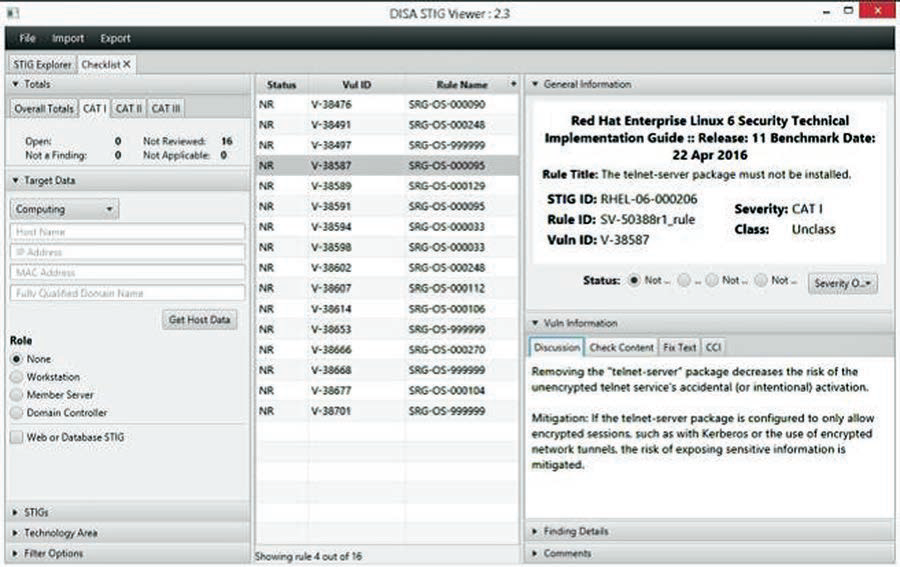
The DISA STIG Viewer is a freely available tool that can be used to complete and document STIG checklists while implementing system security controls. Download it at http://iase.disa.mil/stigs/Pages/stig-viewing-guidance.aspx.
Continuous Monitoring
SIEMS are a product class that can help organizations meet their continuous monitoring requirements through real-time event processing, alerting and reporting. Included in this category are CyberC4:Alert and CyberC4:Guard from RT Logic, a Kratos Subsidiary.
CyberC4:Alert, the first SIEM designed for satellite networks and operations, provides real-time cyber situational awareness for satellite ground networks; and CyberC4:Guard to protect satellite control-related communications across unclassified and classified domains within secure networks.
The use of SIEMs in the commercial sector has become an industry-accepted best practice for monitoring security risks. Real-time alerting helps mitigate the risks associated with vulnerable mission-unique equipment, specialized protocols, untimely patching, and deprecated protocols. Furthermore, scripted active response capabilities allow an organization to fight through a contested network environment.
Smallsat Tip: Challenges associated with implementing a SIEM for a smallsat ground network include: developing custom plug-ins for mission-unique equipment; monitoring specialized protocols, and writing rules and scripts for active responses to detected threats.
Smallsat systems are vulnerable to cyber threats and care should be taken as ground networks are designed. The guidelines and tools presented in this article can help secure smallsat ground networks from potential hackers and cyber threats. Ground operators can benefit from the resources and tools that are broadly in use among Government organizations. NIST Special Publications provide a solid framework for establishing a comprehensive security program.
DISA STIGs and tools can be used to perform and document information assurance hardening of smallsat ground network devices and applications. Security Information and Event Managers and SCAP compliant tools help the organization to continuously monitor security controls on an ongoing basis.
Ted Vera is a Business Area Manager and Cybersecurity Lead at RT Logic, a Kratos company.
References
1Verizon, “Verizon 2016 Data Breach Investigations Report,” Basking Ridge, New Jersey, April 2016
2Intel Security / McAfee, “Net losses: Estimating the Global Cost of Cybercrime,” Santa Clara, California, June, 2014
3Tanase, S., “Satellite Turla: APT Command and Control in the Sky,” September, 2015


